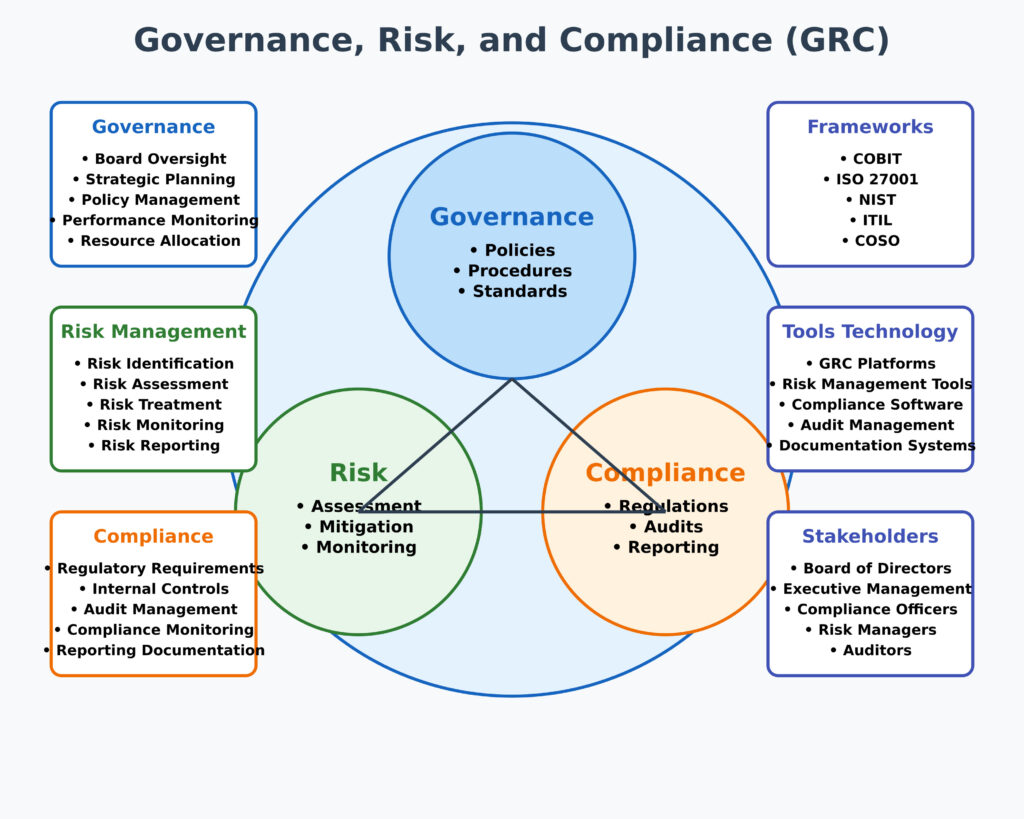
1. Risk Management
Risk Assessment, Mitigation, Acceptance, and Transfer
Risk management is the process of identifying, analyzing, and responding to risk factors throughout the lifecycle of a project or business operation. The key components include:
- Risk Assessment: This involves identifying potential risks and assessing their likelihood and impact. Risk assessment tools like risk matrices or qualitative/quantitative analysis are used to prioritize risks.
- Risk Mitigation: This involves implementing strategies to reduce the likelihood of risks occurring or minimizing their impact. For example, employing multi-factor authentication to mitigate the risk of unauthorized access.
- Risk Acceptance: Sometimes, the cost of mitigating a risk may outweigh the potential damage. In such cases, organizations may choose to accept the risk and monitor it.
- Risk Transfer: Transferring risks involves shifting the risk to another party, often through insurance or outsourcing.
Common Risk Management Frameworks
Several established frameworks guide organizations in managing risks effectively:
- NIST Risk Management Framework (RMF): A structured approach focusing on identifying, assessing, and mitigating risks, particularly in IT systems.
- ISO 31000: Provides principles and guidelines for risk management, applicable across all industries.
- COBIT (Control Objectives for Information and Related Technologies): Focuses on aligning IT risk management with business objectives.
- COSO ERM (Enterprise Risk Management): Integrates risk management with strategic decision-making.
2. Security Policies and Procedures
Importance of Security Awareness Training
Security awareness training is essential for equipping employees with the knowledge and skills to recognize and respond to security threats. Benefits include:
- Reducing the risk of phishing attacks and social engineering.
- Ensuring compliance with regulatory requirements.
- Promoting a culture of security awareness, minimizing insider threats.
- Teaching employees to identify and report suspicious activity, thus strengthening the organization’s security posture.
Change Management Processes
Change management is a systematic approach to managing changes in an organization’s IT environment to minimize risks and ensure stability. Key steps include:
- Change Identification: Document proposed changes, including the purpose and scope.
- Impact Assessment: Evaluate potential risks, costs, and benefits.
- Approval Process: Obtain approvals from stakeholders or a change advisory board (CAB).
- Implementation: Schedule and execute the change with minimal disruption.
- Review: Post-implementation review to assess the change’s success and address issues.
3. Legal and Regulatory Compliance
GDPR (General Data Protection Regulation): A European Union regulation that governs data protection and privacy for individuals. Organizations must:
- Obtain clear consent for data collection.
- Provide individuals with access to their data.
- Report data breaches within 72 hours.
- Implement measures to protect personal data, such as encryption.
HIPAA (Health Insurance Portability and Accountability Act): A U.S. regulation aimed at protecting sensitive patient health information. Requirements include:
- Conducting regular risk assessments.
- Implementing access controls to limit who can view patient data.
- Ensuring secure transmission and storage of electronic health records.
PCI DSS (Payment Card Industry Data Security Standard): A standard for securing credit card transactions and protecting cardholder data. Key requirements include:
- Encrypting cardholder data during transmission.
- Implementing robust access control measures.
- Conducting regular vulnerability scans and penetration testing.
SOX (Sarbanes-Oxley Act): U.S. legislation ensuring the accuracy of financial reporting and protecting against fraud. It mandates:
- Internal controls for financial systems.
- Regular audits and reporting of financial data.
- Executive accountability for financial accuracy.
Understanding Contracts and SLAs
Contracts and Service Level Agreements (SLAs) define the terms, conditions, and expectations of services provided. Key components include:
- Performance Metrics: Specify measurable outcomes, such as uptime and response times.
- Roles and Responsibilities: Clearly define what is expected from each party.
- Remediation Terms: Outline actions if service levels are not met.
- Termination Clauses: Specify conditions under which the agreement can be terminated.
Ensuring compliance with legal, regulatory, and contractual obligations is critical to maintaining trust and avoiding penalties. Organizations must stay updated on regulations and integrate them into their governance frameworks. In the next module you can learn about “Functional controls for information security” .