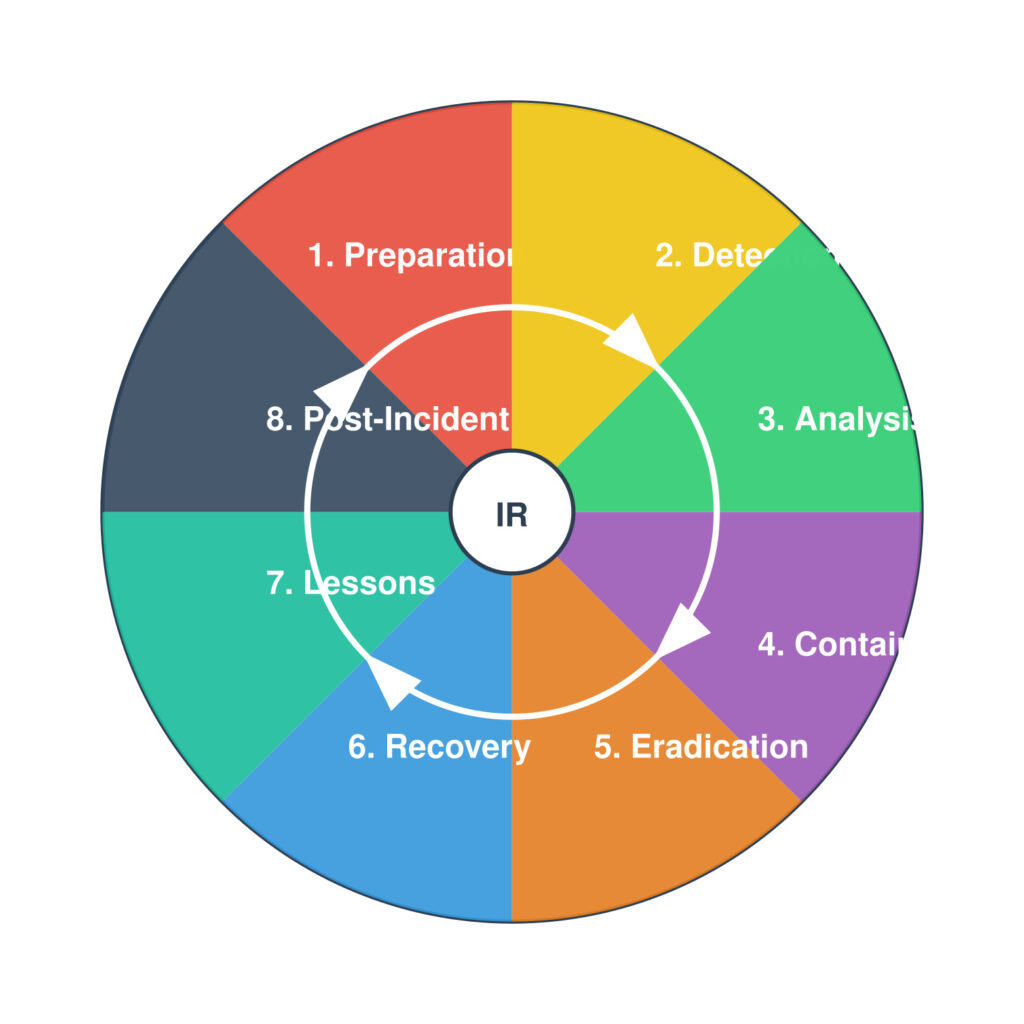
1. Incident Response Process
Incident response is a structured approach to handling security incidents, breaches, and cyber threats. This process ensures quick action to minimize impact and recover operations effectively.
Stages of Incident Response:
| Stage | Description |
|---|---|
| Preparation | Establishing an incident response plan, training staff, and conducting simulations. |
| Identification | Detecting and analyzing the incident to determine its nature and scope. |
| Containment | Isolating affected systems to prevent the threat from spreading. |
| Eradication | Removing the threat completely, such as deleting malware or closing vulnerabilities. |
| Recovery | Restoring systems and services to normal operations, ensuring no residual issues. |
| Lessons Learned | Conducting a post-incident review to improve processes and prevent recurrence. |
Each stage is critical for ensuring that incidents are managed effectively. Organizations must regularly review and update their response plans to address emerging threats.
2. Monitoring Tools
Monitoring tools are essential for identifying potential security threats and maintaining situational awareness within an organization’s IT environment. They allow real-time detection and proactive response to incidents.
Key Monitoring Tools:
- SIEM (Security Information and Event Management):
- Aggregates and analyzes data from various sources such as firewalls, servers, and endpoints.
- Automates threat detection and streamlines compliance reporting.
- Example: Splunk, which provides real-time threat detection and facilitates efficient incident response.
- Packet Analyzers:
- Tools like Wireshark inspect network traffic to identify anomalies and troubleshoot issues.
- These tools help detect suspicious behavior, such as unauthorized access or data exfiltration.
- Vulnerability Scanning Tools:
- Automates the process of identifying weaknesses in systems, networks, and applications.
- Examples:
- Nessus: Highlights outdated software and misconfigurations.
- OpenVAS: Provides detailed vulnerability assessments and mitigation recommendations.
Benefits of Monitoring Tools:
- Early detection of unusual activity and potential threats.
- Improved response times for mitigating risks.
- Simplified compliance with industry regulations and standards.
3. Forensics Basics
Digital forensics plays a vital role in investigating cybersecurity incidents. It involves collecting, preserving, and analyzing electronic evidence to determine the cause and scope of an incident.
Key Aspects of Forensics:
- Evidence Collection:
- Systematic gathering of logs, memory dumps, and other relevant data from compromised systems.
- Tools used: FTK Imager (to capture disk images), EnCase (for comprehensive evidence handling).
- Chain of Custody:
- A detailed record documenting how evidence is collected, stored, and accessed.
- Ensures that evidence remains admissible in legal proceedings.
- Forensic Analysis Tools:
- Analyze digital artifacts such as logs, files, and network traffic.
- Examples:
- Autopsy: Open-source platform for file recovery and analysis.
- Magnet AXIOM: Offers in-depth investigations into mobile, cloud, and endpoint data.
Applications of Forensics:
- Identifying the origin of attacks.
- Gathering evidence for legal actions.
- Preventing future incidents by analyzing vulnerabilities.
4. Backup and Recovery
Backup and recovery strategies are critical for ensuring data availability and operational continuity during and after incidents. A robust backup strategy mitigates the impact of data loss and supports disaster recovery efforts.
Core Concepts:
- Disaster Recovery Plans (DRP):
- Focus on restoring IT systems and data to operational status after an incident.
- Key metrics include:
- Recovery Time Objective (RTO): The maximum acceptable downtime for systems.
- Recovery Point Objective (RPO): The maximum acceptable data loss in terms of time.
- Business Continuity Planning (BCP):
- Ensures that essential business functions can continue during and after disruptions.
- Components include:
- Redundant systems and infrastructure.
- Communication plans for employees and stakeholders.
- Alternate workflows to sustain critical operations.
- Backup Strategies:
- Full Backup: A complete copy of all data, offering comprehensive recovery but requiring significant storage and time.
- Incremental Backup: Backs up only data changed since the last backup, saving storage space but requiring all backups for recovery.
- Differential Backup: Backs up all changes since the last full backup, offering a middle ground between full and incremental backups.
Recommendations for Effective Backup and Recovery:
- Test backups regularly to ensure reliability and quick restoration.
- Follow the 3-2-1 Rule: Maintain 3 copies of your data, store them on 2 different media types, and keep 1 copy offsite.
- Incorporate automated backup solutions to minimize human error and enhance efficiency.
By combining proactive planning, effective tools, and regular updates to strategies, organizations can ensure resilience against incidents and maintain their operations with minimal disruption. In the next module you will learn about “Governance, risk and compliance” .