1. Access Controls implementation
Authentication Methods:
- Passwords: The most common method of authentication implementation, involving a secret combination of characters. Password security relies on complexity, length, and frequent updates.
- Biometrics: Authentication based on unique biological characteristics, such as fingerprints, facial recognition, or iris scans. Biometrics provides strong security but can raise privacy concerns.
- Tokens: Physical or digital devices that generate one-time passwords (OTP) or act as key cards. Examples include hardware tokens like RSA SecurID and software-based tokens like Google Authenticator.
Multifactor Authentication (MFA):
- MFA combines two or more authentication factors to enhance security. Factors can include:
- Something you know (password or PIN).
- Something you have (token or smart card).
- Something you are (biometric data).
- Example: Logging into an account with a password and verifying with an OTP sent to a mobile device.
Role-Based Access Control (RBAC):
- Access is granted based on a user’s role within an organization. Roles define permissions and restrict access to only what’s necessary for a user’s duties.
- Example: A finance employee may access billing software but not HR records.
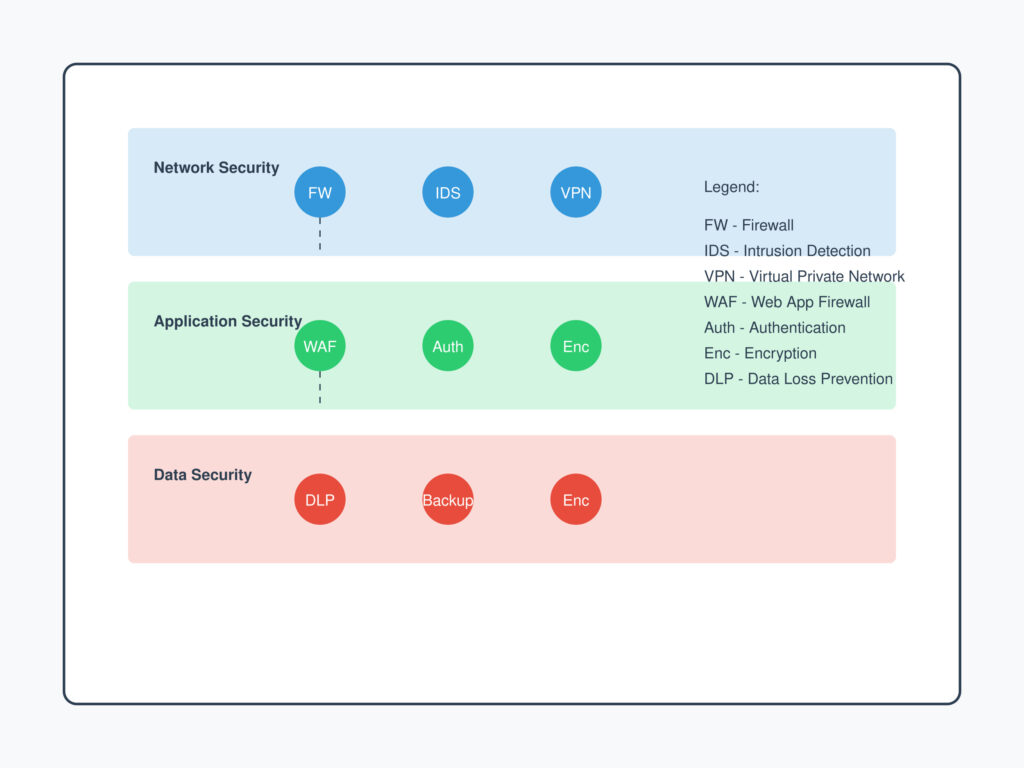
2. Secure Network Implementation
Configuring Firewalls, VPNs, and IDS/IPS:
- Firewalls: Act as a barrier between trusted and untrusted networks, filtering traffic based on rules. Firewalls can be hardware-based, software-based, or cloud-based.
- Virtual Private Networks (VPNs): Encrypt data transmission between devices and networks, ensuring secure communication over public networks. Common VPN protocols include IPsec and OpenVPN.
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): IDS monitors network traffic for suspicious activity and alerts administrators. IPS actively blocks identified threats.
Wireless Security Protocols:
- WPA2: Uses Advanced Encryption Standard (AES) for strong wireless encryption. Widely used but vulnerable to certain attacks like KRACK.
- WPA3: The latest standard with improved encryption and security features, such as forward secrecy and protection against brute-force attacks.
3. Host and Application Security
Endpoint Protection:
- Antivirus Software: Scans and removes malicious software. Modern solutions include real-time protection and heuristic analysis to detect unknown threats.
- Data Loss Prevention (DLP): Prevents sensitive data from being leaked or transferred outside an organization. Examples include monitoring email for unauthorized attachments and restricting USB drive usage.
Secure Coding Practices:
- Input Validation: Ensures that user input is sanitized to prevent injection attacks (e.g., SQL injection, XSS).
- Error Handling: Prevents exposure of sensitive system details through error messages.
- Code Reviews: Regular peer reviews to identify and fix vulnerabilities before deployment.
Patching and Vulnerability Management:
- Patching: Regular updates to fix known vulnerabilities in software and systems. Examples include operating system updates and application patches.
- Vulnerability Scanning: Tools like Nessus and Qualys identify security gaps, helping prioritize patching efforts.
4. Cryptography
Symmetric vs. Asymmetric Encryption:
- Symmetric Encryption: Uses a single key for encryption and decryption. It is fast but requires secure key distribution. Example algorithms: AES, DES.
- Asymmetric Encryption: Uses a pair of keys (public and private). Public keys encrypt data, while private keys decrypt it. Example algorithms: RSA, ECC.
Key Management and PKI:
- Key Management: Ensures secure generation, storage, rotation, and disposal of encryption keys. Poor key management can compromise cryptographic security.
- Public Key Infrastructure (PKI): A framework for managing digital certificates and public-private key pairs. PKI enables secure communication and authentication through trusted certificate authorities (CAs).
Common Cryptographic Protocols:
- TLS (Transport Layer Security): Secures data transmission over the internet. Used in HTTPS, email encryption, and VPNs.
- HTTPS (HyperText Transfer Protocol Secure): Ensures secure communication between web browsers and servers. It uses TLS to encrypt data.
- S/MIME (Secure/Multipurpose Internet Mail Extensions): Provides email encryption and digital signatures.
This module provides foundational knowledge for implementing robust security measures across systems, networks, and applications. In the next module you can learn about “operations and incident response “