Cybersecurity begins with understanding the threats and vulnerabilities an organization may face. This module covers the different types of threats, common attacks, and strategies for managing vulnerabilities effectively.
1. Understanding Threats
Types of Attackers
- Script Kiddies:
- Unskilled individuals who use pre-written scripts or tools to carry out attacks.
- Example: Using a free Distributed Denial of Service (DDoS) tool to overwhelm a small website.
- Insiders:
- Employees or contractors with legitimate access who misuse their privileges.
- Example: An employee copying sensitive data to a USB drive and sharing it with competitors.
- Hacktivists:
- Cyber attackers driven by political, social, or ideological motives.
- Example: Defacing a government website to protest policies.
- Cybercriminals:
- Organized groups focused on financial gain through theft or extortion.
- Example: Launching ransomware attacks to demand payment in cryptocurrency.
- Nation-State Actors:
- State-sponsored attackers aiming to disrupt or spy on other countries.
- Example: A nation-state launching a cyber-espionage campaign to steal defense secrets.
Common Threat Vectors
- Email: Phishing attacks use malicious emails to steal credentials or deliver malware.
- Websites: Drive-by downloads exploit vulnerabilities in browsers or plugins.
- Removable Media: USB drives infected with malware.
- Unpatched Software: Attackers exploit outdated systems lacking security updates.
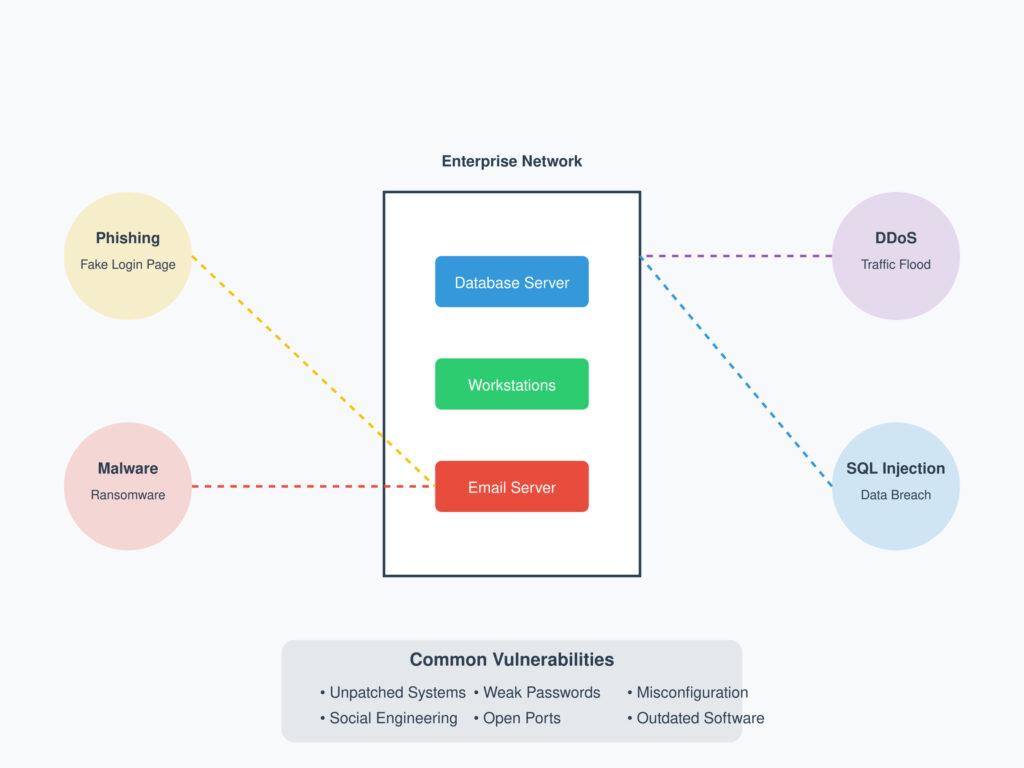
2. Types of Attacks
Social Engineering Attacks
- Phishing: Deceptive emails designed to trick users into revealing sensitive information.
- Example: An email pretending to be from a bank, asking the recipient to log in via a fake link.
- Pretexting: Creating a fabricated scenario to steal information.
- Example: Posing as IT support to get an employee’s login credentials.
- Tailgating: Following an authorized person into a restricted area.
- Example: An attacker gains physical access to a server room by following an employee who uses their keycard.
Malware Types
- Viruses: Malicious programs that replicate and spread.
- Example: The Melissa virus, which spread via email attachments.
- Worms: Standalone malware that spreads without user intervention.
- Example: The WannaCry ransomware worm.
- Ransomware: Encrypts data and demands payment for decryption keys.
- Example: CryptoLocker ransomware attack.
Network Attacks
- Distributed Denial of Service (DDoS): Overwhelming a network or server with traffic.
- Example: Botnets flooding an online store during a sale event.
- Man-in-the-Middle (MitM): Intercepting communications between two parties.
- Example: Intercepting unencrypted emails on a public Wi-Fi network.
- ARP Poisoning: Spoofing MAC addresses to redirect traffic to a malicious system.
- Example: Redirecting internal communications to a rogue device.
Cryptographic Attacks
- Replay: Reusing valid data transmission to trick systems.
- Example: Capturing a legitimate login session and reusing it to bypass authentication.
- Brute Force: Attempting all possible password combinations to gain access.
- Example: Cracking a poorly secured admin account using an automated tool.
3. Vulnerability Management
Common Vulnerabilities and Exploits
- Outdated Software:
- Example: Exploiting old versions of Windows vulnerable to EternalBlue.
- Weak Passwords:
- Example: Brute-forcing accounts with predictable passwords like “123456.”
- Misconfigured Systems:
- Example: Leaving default credentials on a router, allowing attackers to gain administrative access.
Tools for Vulnerability Assessment
- Nessus:
- What it Does: A widely used vulnerability scanner that identifies misconfigurations, outdated software, and missing patches.
- Example Use Case: Scanning a corporate network to detect systems vulnerable to WannaCry ransomware.
- OpenVAS:
- What it Does: Open-source tool that performs comprehensive vulnerability scanning and reporting.
- Example Use Case: Evaluating a web server to find outdated SSL/TLS protocols.
Vulnerability Management in Action
Let’s consider a practical scenario:
- Situation: A financial institution wants to secure its network.
- Step 1: Use Nessus to scan all devices for vulnerabilities.
- Step 2: Identify outdated firewalls and software.
- Step 3: Mitigate risks by applying patches and reconfiguring firewalls.
- Step 4: Use OpenVAS to validate fixes and ensure no critical vulnerabilities remain.
By understanding threats, recognizing attacks, and managing vulnerabilities, you build a robust defense against cybersecurity challenges. In the next module, we’ll dive into “Architecture and Design“ to explore how secure systems are built.