Configuring LDAPS and Restricting LDAP Bindings
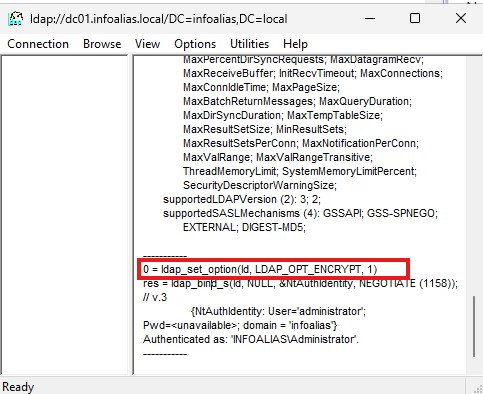
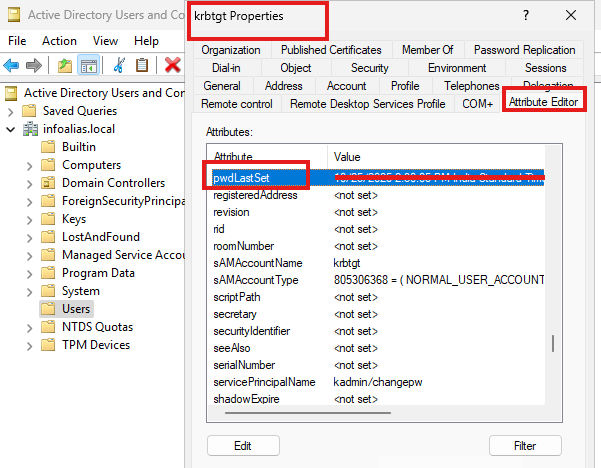
In today’s enterprise environments, securing directory services is a critical step in protecting authentication data and sensitive organizational information. By default, LDAP (Lightweight Directory Access Protocol) communication occurs in clear…